
DNSpooq - Kaminsky attack is back!
7 new vulnerabilities are being disclosed in common DNS software dnsmasq, reminiscent of 2008 weaknesses in Internet DNS Architecture
Overview- DNSpooq
Vulnerabilities threaten DNS integrity (again)
The JSOF research labs are reporting 7 vulnerabilities found in dnsmasq, an open-source DNS forwarding software in common use. Dnsmasq is very popular, and we have identified approximately 40 vendors whom we believe use dnsmasq in their products, as well as major Linux distributions.
The DNS protocol has a history of vulnerabilities dating back to the famous 2008 Kaminsky attack. Nevertheless, a large part of the Internet still relies on DNS as a source of integrity, in the same way it has for over a decade, and is therefore exposed to attacks that can endanger the integrity of parts of the web.
DNSpooq
The Dnspooq vulnerabilities include DNS cache poisoning vulnerabilities as well as a potential Remote code execution and others. The list of devices using dnsmasq is long and varied. According to our internet-based research, prominent users of dnsmasq seem to include Cisco routers, Android phones, Aruba devices, Technicolor, and Red-Hat, as well as Siemens, Ubiquiti networks, Comcast, and others listed below. Depending on how they use dnsmasq, devices may be more or less affected, or not affected at all.
The origin of the name DNSpooq is a merge of 3 elements: DNS spoofing, the idea of a spook spying on Internet traffic, and the ‘q’ at the end of dnsmasq, replacing the ‘k’ of spook with a ‘q’. The spy or spook graphic illustrates the effects of an effective DNS spoofing on the ability to spy on internet traffic. The JSOF-pink glasses show how looking through tainted glasses, or a compromised middleman may alter your perception of the reality.
DNSpooq demonstrates that DNS implementations are still insecure, even today, 13 years after the last major attack was described.
Given the vulnerabilities in DNS over the years, you would think that the security-enhancement mechanisms that have been developed in response, would be ubiquitous by now. However, in reality, DNSSEC is still not very widely deployed, and neither is HSTS. For example, according to research from 2017, adoption of HSTS among the 1M most popular websites was only at about 5%). According to some rough estimates performed by JSOF with the help of large Internet companies, and matching external sources, around 15-20% of Internet traffic is still completely unencrypted, and users still click through to insecure websites.
Credit and Appreciation
DNSpooq disclosure was made possible through coordination of many different participants. Special appreciation for their efforts must be expressed to:
- Help with disclosure coordination and fix efforts:
- Vijay Sarvepalli (CERT Coordination Center [Cert/CC])
- Disclosure coordination and vulnerability communication:
- Help with patch development:
- ICS-CERT coordination: Daniel Larson (ICS-CERT)
- Patch creation and vulnerability responsiveness: Simon Kelley
- PR and communications: Zachary Weiner
- Proofreading: Ariel Schön from JSOF
- Publication and disclosure communication: Sari Heyman from JSOF
- Research: Moshe Kol and Shlomi Oberman from JSOF
History
In 2008, well-known security researcher Dan Kaminsky found and disclosed a fundamental flaw in the Internet naming scheme that affected the most common DNS software and the integrity of the way the Internet worked at the time.
Kaminsky proved that attackers can impersonate any website name and steal data. (This has since become known as the “Kaminsky Attack”).
DNS has been considered a somewhat insecure protocol for decades, ever since the Kaminsky disclosure and even before that, though it is assumed to guarantee a certain level of integrity. This is the reason it is still heavily relied upon. At the same time, mechanisms have been developed to improve the security of the original DNS protocol. These mechanisms include HTTPS, HSTS, DNSSEC, and other initiatives. Browsers also try to increase users awareness by alerting them before accessing insecure sites with messages such as “Your Connection is Not Private”.
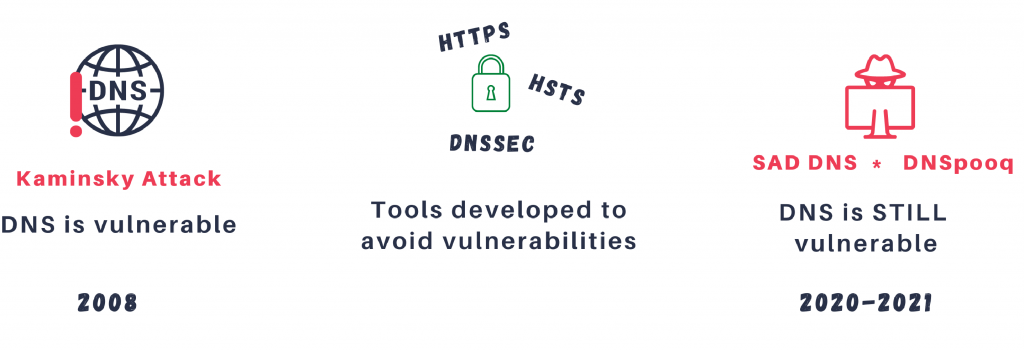
Nevertheless, even with all these mechanisms in place, a DNS hijack is still a dangerous attack in 2021. A large part of the Internet still relies on DNS in a similar manner as in 2008, and is exposed to attacks of the same types.

Impact
The DNSpooq vulnerability set divides into 2 types of vulnerabilities:
- DNS cache poisoning attacks, similar to the Kaminsky attack, but different in some aspects.
- Buffer overflow vulnerabilities that could lead to remote code execution.
(1) DNS Cache Poisoning: The impact of DNS cache poisoning of the routing equipment DNS forwarding server can potentially lead to different kinds of fraud if users believe they are browsing to one website but are actually routed to another.
Traffic that might be subverted includes regular Internet browsing as well as other types of traffic, such as emails, SSH, remote desktop, RDP video and voice calls, software updates, and so on. Some of these protocols have built-in measures to mitigate this type of attack, with varying degrees of effectiveness and so YMMV (Your mileage may vary).
DNS Cache Poisoning
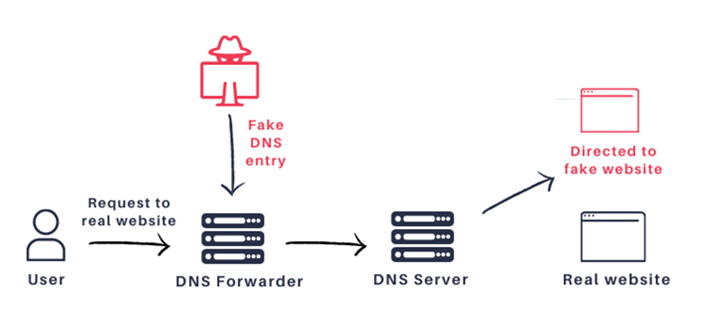
(2) Device take over: In addition to cache poisoning, every device on which an attacker can perform DNS cache poisoning can also potentially be taken over by the attacker. For example, in the case of a router, the attacker would then have complete control over all traffic going in and out of the network.
There are additional impacts possible for these types of attacks. These are hypotheticals, since to our knowledge they have never been performed by a malicious actor in this way, but they are a definite possibility if the vulnerabilities are exploited correctly. Even so, given the hypothetical nature of the situation, it is hard to analyze how likely they are to actually occur and what value they could bring to different malicious actors. These possibilities include:
(A) Massive DDOS: Diversion of a large amount of web-traffic to an attacker-controlled website could be used to generate massive JavaScript-fueled Distributed Denial of Service attacks. Simplistic calculations show that the size of the attack could be on the same order of magnitude as the biggest DDOS attacks performed to date.
Massive DDOS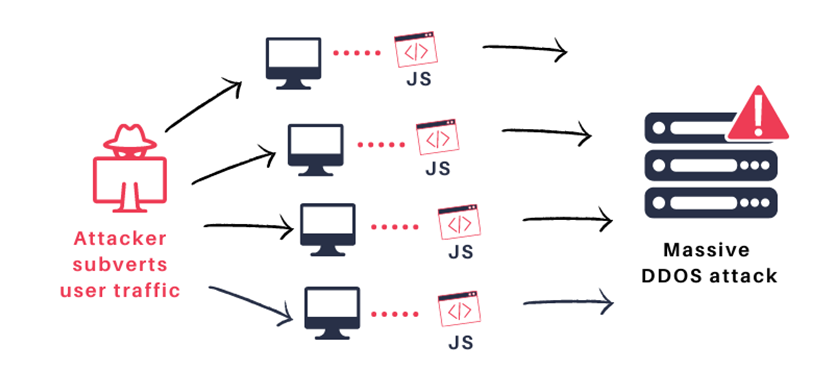
(B) Reverse DDOS: Prevention of certain users from accessing a website and logging of access attempts to a domain.
Reverse DDOS

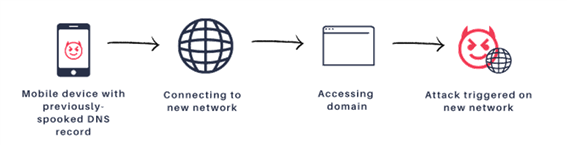
(C) “Semi-Wormable” attacks: In situations where a mobile device moves between networks, the attack may be semi-wormable. It is not wormable in the traditional sense, since there are some pre-conditions and efforts needed on the attacker side for the exploit replication, but is semi-wormable in the sense that the exploit can continue to spread between vulnerable devices without explicit user interaction and without need for additional attacker access. In this scenario, a mobile device that was previously browsing in a network which uses an infected dnsmasq server receives a bad DNS record. When the device reaches a new network, it could infect the new network as well.
Last paragraph’s wording has been edited for clarity following peer feedback.
Wormable Attacks
Technical Overview
Below are high-level technical details of the Vulnerabilities. For in depth information, please refer to our technical whitepaper.
Terminology
DNS: DNS (Domain Name System) is an addressing system used in order to reach a domain. A name such as ‘www.example.com’ would be mapped to an IP address. The DNS protocol is based on queries asking where an address is located and responses containing an IP address. This is a basic feature of the Internet and is used by almost all computer software.
Dnsmasq: Dnsmasq is a popular software used for caching of DNS responses. Storing the responses to previously asked DNS queries locally speeds up the DNS resolution process.
The software is installed on many home and commercial routers and servers in many organizations. Dnsmasq is used heavily by networking equipment, as well as being set up manually by IT personnel, usually in smaller networks. There are other uses of dnsmasq, such as providing DNS services to support Wi-Fi hot-spots, enterprise guest networks, virtualization, ad blocking, implementing a captive portal – the login screen that appears when logging in to a network in an airport or other public location and other use cases.
The DNSpooq vulnerability set divides into 2 types of vulnerabilities:
- DNS cache poisoning attacks, similar to the Kaminsky attack, but different in some aspects.
- Buffer overflow vulnerabilities that could lead to remote code execution.
Cache Poisoning Vulnerabilities
This type of attack allows subverting of DNS queries in an organization or device using dnsmasq. Essentially, this means that an attacker will be able to reroute communications made by a specific target that relies on a website name such as www.example.com.
These vulnerabilities are similar to the SAD DNS attacks reported recently by researchers at UC Riverside and Tsinghua University. SAD DNS also affect dnsmasq and other prevalent DNS software. The SAD DNS and DNSpooq vulnerabilities can also be combined to make attacks even easier. Additional attacks with unclear implications were also reported by a joint effort of universities (Poison Over Troubled Forwarders and others).
The DNSpooq cache poisoning vulnerabilities are labeled:
CVE-2020-25686, CVE-2020-25684, CVE-2020-25685
The vulnerabilities work by reducing the entropy of the TXID and source port. They should be randomized and provide 32 bits of entropy, however, due to the use of a weak hash to identify the DNS requests and a loose matching of request to response, the entropy can be greatly reduced and only ~19 bits need to be guessed, making cache poisoning very feasible. The way that dnsmasq treats CNAME records further allows to spoof a chain of CNAME records and effectively poison 9 DNS records at the same time. To execute the attack a suitable setup must be set in place by the attacker, which is not difficult to perform. For the cache poisoning, devices that do not use the cache feature of Dnsmasq will be much less affected (but not completely immune).
For more detailed technical information, refer to the technical whitepaper.
Buffer Overflow Vulnerabilities
The 4 buffer overflow vulnerabilities that are a part of DNSpooq have a different effect. The worst of these vulnerabilities could lead to a remote code execution on the vulnerable device. These vulnerabilities, in and of themselves, would pose only limited risk. But they become especially powerful since they can be combined with the cache-poisoning vulnerabilities to produce a more potent attack.
These vulnerabilities are labeled:
CVE-2020-25687, CVE-2020-25683, CVE-2020-25682, CVE-2020-25681
The buffer overflow vulnerabilities include a high severity heap-based buffer overflow vulnerability that could potentially lead to remote code execution when dnsmasq is configured to use DNSSEC. The vulnerability resides in the early stages of DNSSEC validation, rendering DNSSEC’s defense against DNS attacks ineffective. We have not attempted full exploitation of this vulnerability. Other vulnerabilities we found are heap-based buffer overflows that can only lead to denial-of-service when DNSSEC is used.
For the Buffer Overflows and Remote Code execution, devices that don’t use the DNSSEC feature will be immune. DNSSEC is a security feature meant to prevent cache poisoning attacks and so we would not recommend turning it off, but rather updating to the newest version of dnsmasq.
For more detailed technical information, refer to the technical whitepaper.
A combination with Impact
One of the interesting things about these vulnerabilities is that each one of them, on its own, has limited impact. However, the vulnerabilities could be combined and chained in certain ways to build extremely effective multi-staged attacks. This is because exploiting some of the vulnerabilities makes it easier to exploit others. For example, we found that combining CVE-2020-25682, CVE-2020-25684, and CVE-2020-25686 would result in CVE-2020-25682 having a lower attack complexity (with the same impact) and result in a combined CVSS of 9.8 according to our analysis (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H ).
Combining the vulnerabilities found by JSOF with other recently-disclosed network attacks could potentially lead to much easier and more widespread attack possibilities, an area of research which can be explored further. This includes vulnerabilities such as NAT-slipstreaming, found by Samy Kamkar, SAD DNS, found by researchers at University of California Riverside, and the lack of destination-side source address validation as found by researchers at Brigham Young University, as well as other academic research on DNS.
Vulnerabilities List
| Name | CVSS | Description |
|---|---|---|
| CVE-2020-25681 | 8.1 | Dnsmasq versions before 2.83are susceptible to a heap-based buffer overflow in sort_rrset() when DNSSEC is used. This can allow a remote attacker to write arbitrary data into target device’s memory that can lead to memory corruption and other unexpected behaviors on the target device. |
| CVE-2020-25682 | 8.1 | Dnsmasq versions before 2.83 are susceptible to buffer overflow in extract_name() function due to missing length check, when DNSSEC is enabled. This can allow a remote attacker to cause memory corruption on the target device. |
| CVE-2020-25683 | 5.9 | Dnsmasq versions before 2.83 are susceptible to a heap-based buffer overflow when DNSSEC is enabled. A remote attacker, who can create valid DNS replies, could use this flaw to cause an overflow in a heap-allocated memory. This flaw is caused by the lack of length checks in rfc1035.c:extract_name(), which could be abused to make the code execute memcpy() with a negative size in get_rdata() and cause a crash in dnsmasq, resulting in a Denial of Service. |
| CVE-2020-25687 | 5.9 | Dnsmasq versions before 2.83are vulnerable to a heap-based buffer overflow with large memcpy in sort_rrset() when DNSSEC is enabled. A remote attacker, who can create valid DNS replies, could use this flaw to cause an overflow in a heap-allocated memory. This flaw is caused by the lack of length checks in rfc1035.c:extract_name(), which could be abused to make the code execute memcpy() with a negative size in sort_rrset() and cause a crash in dnsmasq, resulting in a Denial of Service. |
| CVE-2020-25684 | 4 | A lack of proper address/port check implemented in dnsmasq versions < 2.83 reply_query function makes it easier to forge replies to an off-path attacker. |
| CVE-2020-25685 | 4 | A lack of query resource name (RRNAME) checks implemented in dnsmasq’s versions before 2.83 reply_query function allows remote attackers to spoof DNS traffic that can lead to DNS cache poisoning. |
| CVE-2020-25686 | 4 | Multiple DNS query requests for the same resource name (RRNAME) by dnsmasq versions before 2.83 allows for remote attackers to spoof DNS traffic, using a birthday attack (RFC 5452), that can lead to DNS cache poisoning. |
Vendors
Some of the bigger users of dnsmasq to our understanding and according to our internet research are Android/Google, Comcast, Cisco, Redhat, netgear, and Ubiquiti. There are many more. Different vendors use it for different purposes. Some vendor configurations may not be vulnerable. The following table provides examples of over 40 companies and respective products we believe are using dnsmasq, together with the relevant sources that led us to this understanding.
Attack Scenarios
There are several possible attack scenarios, depending on the device configuration. These include:
- Open forwarders: For the approximately 1 million dnsmasq servers openly visible on the Internet (according to Shodan), attacks through the Internet are very simple. This may be possible in some cases, (we believe rare), even if the forwarder is not open to the Internet.
- Closed network with internal attacker: If a dnsmasq server is only configured to listen to connections received from within an internal network, and an attacker gains a foothold on any device in the network, the attacker would be able to perform the attack.
- Browser-based attack: This variation of the attack is more complex to pull off but is much more dangerous, since the attack can be performed with only a basic level of access. Even if a dnsmasq server is closed off to the outside world, and is only configured to listen to connection received from within an internal network, if attackers are able to get a device within the network to browse to their website, they could perform the attack this way. This includes cases where only a part of the website is crafted by the attacker, such as if the attacker were able to display crafted ads in a victim’s browser through an ad network. This version of the attack is more complex, may take some time, may have lower success rates, and will not work on every browser. For example, this method has been tested and shown to work on an iPhone with built-in Safari, working on a single device. It did not work in Chrome running on Windows. We have not completed extensive tests, but believe that Chrome is probably immune. Chromium-base browsers and Microsoft browsers were not tested.
- Open Wi-Fi or wired network: If a dnsmasq server is only configured to listen to connections received from within an internal network but the network is open, such as an airport network or a corporate guest network, an attacker will be able to perform the attack.
Disclosure
The story of DNSpooq begins in the summer of 2020, when we began researching dnsmasq vulnerabilities. We identified some vulnerabilities and moved forward to reproduce them under different configurations. Once we validated the vulnerabilities, we kicked off a coordinated vulnerability disclosure (CVD) process. Given how dependent the Internet is on DNS technology, and how widespread dnsmasq, is we certainly believe the situation is of high importance to home users and enterprises.
The disclosure started on August 2020 and the Embargo ended on January 2021, marking approximately 5 months in total of Coordination of the vulnerabilities.
With the help of CERT/CC and volunteers from several companies, a working group was formed, combining the expertise and extended reach of members from JSOF, CERT/CC, Cisco, Google, Red Hat, Pi-hole, and Simon Kelley, the maintainer of dnsmasq, to ensure that the DNSpooq vulnerabilities would be effectively fixed and well documented and communicated.
Since we are coordinated DNSpooq through CERT/CC, we do not have direct visibility into what the various vendors will decide to do, in terms of integrating patches and fixes to their customers. Generally, we believe the major OS distributors and vendors will issue patches simultaneously, and the other vendors publish updates soon afterwards.
Mitigation and Workarounds
While several workarounds exist, and are documented in our technical whitepaper, the best and only full mitigation is to update dnsmasq to version 2.83 or above.
Summary
DNSpooq is a series of vulnerabilities found in the ubiquitous open-source software dnsmasq, demonstrating that DNS is still insecure, 13 years after the last major attack was described.
Some of the DNSpooq vulnerabilities allow for DNS cache poisoning and one of the DNSpooq vulnerabilities could permit a potential Remote Code execution that could allow a takeover of many brands of home routers and other networking equipment, with millions of devices affected, and over a million instances directly exposed to the Internet.
